SSH Foo
Last week, I gave a presentation at a local LUG (which is a Linux User’s Group, for anyone who hasn’t heard of those before) on the subject of SSH Foo.
In UNIX circles, we refer to tricks of the trade as “Kung Fu” or just “Fu” (which sounds rude), so it is spelled “Foo” ;-)
In this blog post, I’ll summarize my SSH Foo talk! Be aware that this is not an introduction to SSH, but a more advanced look at some interesting SSH features for those who are already comfortable with it. As such, I’ve kept to point form here to allow you to skim to the parts you are most interested in!
Part 1 - Cryptography Basics:
Symmetric cryptography (e.g. AES/Blowfish/RC4):
- Fast for encrypting payloads of data
- However, negotiating the symmetric key across a network is difficult
- Clients usually generate a symmetric key and encrypt it asymmetrically to get it to a server across a network

Asymmetric cryptography (e.g. RSA/DSA/ECC):
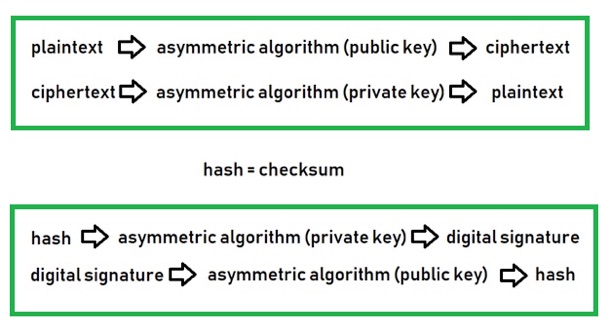
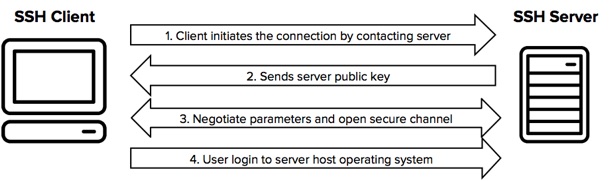
Part 2 - SSH Basics:
- Encrypted telnet (telnet towel.blinkenlights.nl) but without Star Wars
- Uses symmetric encryption for all payload data
- Uses asymmetric encryption to protect symmetric key generated by the SSH client
-
Symmetric encryption controlled by client
/etc/ssh/ssh_config Ciphers (usually AES*) -
Asymmetric encryption controlled by server (the host keys):
/etc/ssh/sshd_config HostKey /etc/ssh/ssh_host_rsa_key (& .pub) HostKey /etc/ssh/ssh_host_ecdsa_key (& .pub) HostKey /etc/ssh/ssh_host_ed25519_key (& .pub) ~/.ssh/known_hosts
Part 3 - SSH User Keys:
-
You can also create asymmetric keys for your local user account and add these keys to each server you manage to avoid passwords
ssh-keygen -
Do you want to protect your private key with passphrase? You’ll need it each time the private key is used unless you want to load a program that caches it, such as ssh-agent
cat ~/.ssh/id_rsa cat ~/.ssh/id_rsa.pub ssh-copy-id -i root@server1 ssh root@server1 (look ma, no password!) -
Many systems prevent root SSH in sshd_config (must connect as bob and su/sudo):
PermitRootLogins yes/no/without-password -
If you want to omit the username for each host, you can use host-specific options on your SSH client to specify a default user:
cat ~/.ssh/config Host server1 User admin Host server2 User bob
Part 4 - SSH File Copy:
-
Copy remote /root/lala file (on server1) to local /var directory
ssh root@server1 cat /root/lala > /var/sample scp root@server1:/root/lala /var -
Copy the local /root/lala file to /var directory on remote computer (server1)
ssh root@server1 cat </root/lala ">" /var/lala scp /root/lala root@server1:/var -
Can also use piping
dd if=/root/lala | ssh -C user@host dd of=/var/lala -
Works for anything, really
dd if=/dev/tty5 | ssh -C user@host dd of=/dev/tty2
Part 5 - Tunnelling:
-
Tunnelling X.org (requires xauth)
ssh –X root@server1 gnome-control-center& -
Tunneling other stuff (e.g. VNC) can be done using one of two methods.
-
Method 1: Local tunneling – e.g. forward local traffic on port 5999 to server1 on port 5900 as bob:
ssh -L 5999:localhost:5900 bob@server1 //After this, you can start a VNC viewer and connect to localhost:5999 //to access the VNC server running on port 5900 on server1 through an //SSH tunnel -
Method 2: Remote tunneling – e.g. bob on client1 can start a VNC viewer and connect to server1:5999 in order to access the VNC server running on port 5900 on server1 (your server) via SSH:
ssh -R 5999:server1:5900 bob@client1 -
Evading firewall restrictions with local tunneling:
ssh homeserver –L 443:lala.com:443 cat /etc/hosts (127.0.0.1 lala.com) apachectl stop curl https://lala.com //General format (you are computerA): ssh computerB –L 443:computerC:443
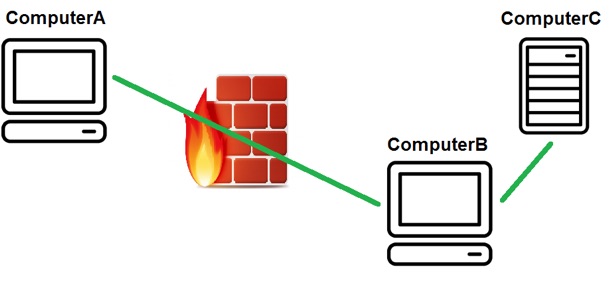
-
Can also tell SSH to do SOCKS5 proxy forwarding to a home server to evade a firewall:
ssh -D 8080 homeserver //Set Chrome/Firefox proxy address to localhost:8080 //DNS requests are not part of this (you can tunnel DNS through a SOCKS5 proxy //with other software like DNSCrypt or a Firefox plugin) -
Problems?
grep Forwarding /etc/ssh/sshd_config X11Forwarding no AllowTcpForwarding no
Part 6 - SSHFS (NFS is sooooo yesterday):
-
Access remote / filesystem on server1 over SSH session mounted to local /mnt directory:
dnf install sshfs sshfs root@server1:/ /mnt ls /mnt rm –Rf /mnt/* (--no-preserve-root bypassed)